CryptoPhoto PAM module setup
Before being able to deploy the CryptoPhoto PAM module, you can register a new CryptoPhoto administration account and obtain API Keys, which will be used to configure the CryptoPhoto PAM module.
Creating and configuring a CryptoPhoto administration account is described here.
Downloading and Installing the CryptoPhoto PAM module
-
Download the pre-build RPM (64 bit): pam-cryptophoto-1.20180806-rc4.x86_64.rpm
If the yum package management utility is present
yum install pam-cryptophoto-1.20180806-rc4.x86_64.rpm
or on systems providing the rpm package management utility
rpm -ivh pam-cryptophoto-1.20180806-rc4.x86_64.rpm
Configuration for the PAM module
PAM module configuration and service protection is managed by the cp_pam_config utility (this requires root access).
For configuring the PAM module type in console:
cp_pam_config --setup
This will start an interactive setup which will ask you to provide information regarding the CryptoPhoto provider details, URLs used for retrieving the verification results and PAM module behavior settings.
You will be asked the following questions:
-
Do you wish to use the global CryptoPhoto PAM provider? [yes/no][default no]: yes
If you don't have an account registered with CryptoPhoto you can use the global provided one. Having a personal account allows you to customize the PAM access verification template.
-
--- CryptoPhoto server or appliance URL value = https://cryptophoto.com
Leave the default to use the CryptoPhoto cloud. Only enter your own appliance URL if you operate your own CryptoPhoto appliance
-
--- Provider public key value = 7c34907fe8a9cb0e184dab64b6bf94a00457b6d2642b5a3b --- Provider private key value = a3d24d6de7d065e7f6c9d2c6093bef49168c79d78f6e60a2
You will find these values in your CryptoPhoto account.
-
--- Callback URL where CryptoPhoto should send the access verification result value = https://cryptophoto.com/pam_push?id= --- Long pull URL where the PAM module/tools wait for CryptoPhoto responses value = https://cryptophoto.com/pam_pull?id=
push and pull URLs used by the PAM module to send/receive data from CryptoPhoto.
-
--- Timeout for CURL requests (in seconds) [int][default: 15]:
How much time to wait for CryptoPhoto requests to complete.
-
--- Should users that don't have CryptoPhoto setup be allowed access? [yes/no][default no]:
If you answer no, only users who have CryptoPhoto setup will be allowed access to a service after a successful verification.
If you answer yes then users who have CryptoPhoto setup (and a token enrolled) will be verified before gaining access to a service. All other users will be allowed access by default. -
--- Should users be allowed access in case of an internal error? [yes/no][default no]:
The settings specifies what happens when a CryptoPhoto request fails or a timout occurs.
-
-- Should CryptoPhoto be globally required (regardless of user settings)? [yes/no][default yes]:
The settings enforces CryptoPhoto verification for all users who have CryptoPhoto setup.
-
--- Error emails recipient [where shall we send notices of any errors that occur?] [email]: admin@domain.com value = admin@domain.com --- Error emails sender [this will be the 'From:' email name for messages sent to the above recipient] [email][default: CryptoPhoto PAM Error <cppamerr@domain.com>]: value = CryptoPhoto PAM Error <cppamerr@domain.com> --- sendmail path [string][default: /usr/sbin/sendmail]: value = /usr/sbin/sendmail
Recipient and sender setup for emails regarding CryptoPhoto errors.
If you answered yes above the following questions will be skipped.
CryptoPhoto protection user setup
In order to use the CryptoPhoto protection, users must have the CryptoPhoto app installed and also must have a CryptoPhoto token registered. The token enroll is a two steps process, both accomplished using the cp_pam_user utility:
-
A server administrator performs the initial CryptoPhoto user setup. This generates an unique ID for the user and retrieves an enrollemnt code from the CryptoPhoto server: (must be run as root)
cp_pam_user --setup --user user1
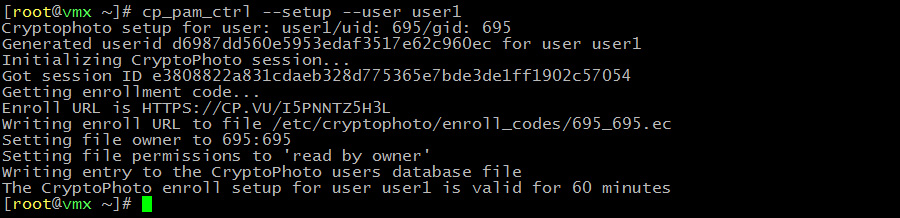
Note: The setup is only accessbile for user1
-
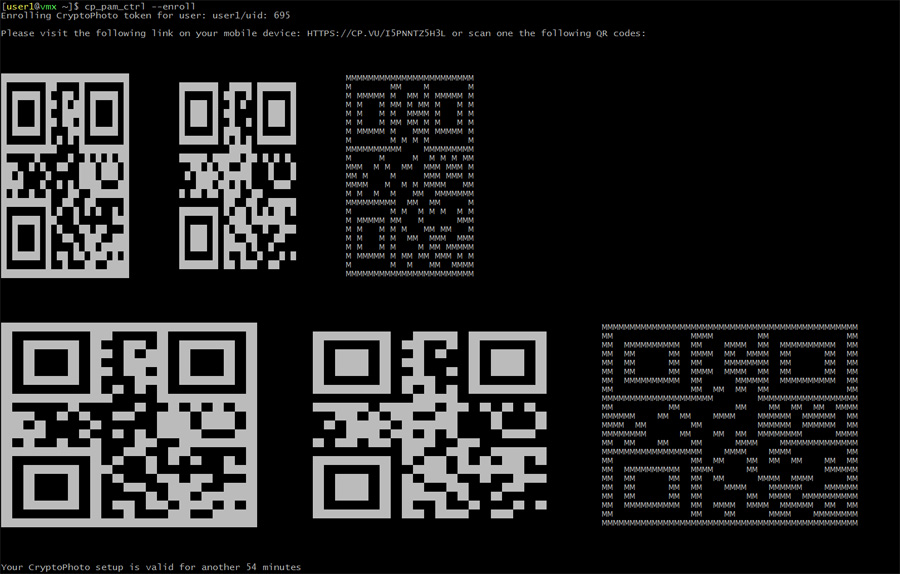
Now user1 can enroll the token by issuing the following command:
cp_pam_user --enroll
Managing CryptoPhoto protection for services
The cp_pam_config utility is also used for enabling/disabling/checking the status of protected services:
-
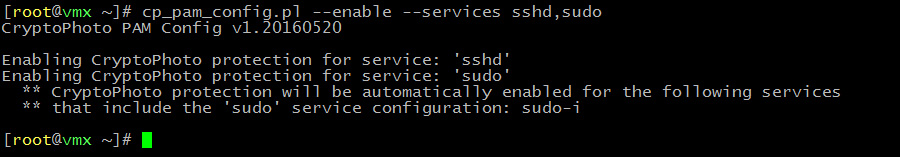
Enable CryptoPhoto protection:
cp_pam_config --enable --services service1,service2
-
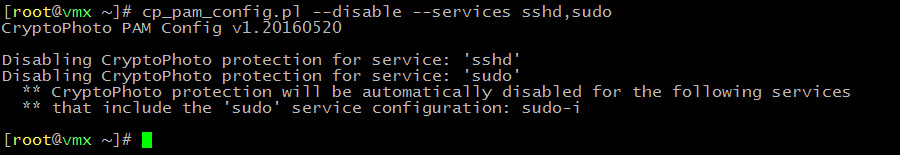
Disable CryptoPhoto protection:
cp_pam_config --disable --services service1,service2
-
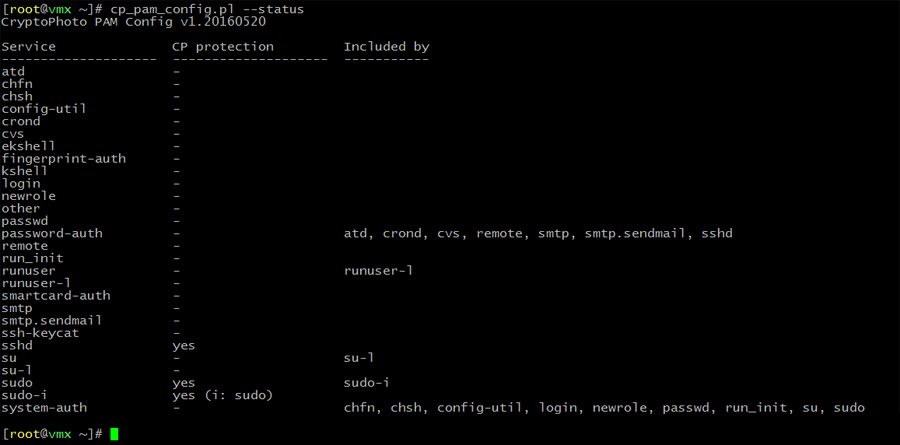
Check the status of CryptoPhoto protection:
cp_pam_config --status
Uninstall CryptoPhoto PAM module
To uninstall the CryptoPhoto PAM module run the following commands:
cp_pam_config --uninstall
This will remove the configuration file and user database.
If you installed the module using the RPM package:
yum remove pam-cryptophoto-1.20180806-rc4.x86_64.rpm
or
rpm -ev pam-cryptophoto-1.20180806-rc4.x86_64.rpm
If you built and installed the module from source:
make uninstall
Video
Activating 2FA in Linux for SSH, SUDO, SU and other services using PAM with CryptoPhoto
 Loading ...
Loading ...